- Information SECURITY
How the shifting threatscape demands comprehensive security risk management
What ostensibly appears to be a well-orchestrated cyber-attack on U.S. software supplier Collins Aerospace’s ubiquitously deployed product “Muse” for managing traveler baggage beginning on the evening of 19 September 2025 is not an isolated incident. Not only did this most recent attack affect multiple airports, i.e. Heathrow, Berlin, Brussels and Dublin. This attack is – more importantly – one in a string of offensive actions targeting European infrastructure and supply chains.
To name just a few recent examples:
- Last week Jaguar Landrover’s supply chain and production capability was brought to a grinding halt. The impact of the attack appears to persist.
- In June this year, though a potential catastrophe was averted just in time, a sophisticated prompt-inject attack dubbed “Echoleak” targeted Copilot, a widely deployed corporate large natural language model (LLM) that is part of the Microsoft eco-system and with varying degrees of access to corporate data.
- UK retailer Marks & Spencer earlier this year was almost brought to its knees in a cyber attack via a human vulnerability on its time-sensitive supply chain and that reportedly will cost it a third of its annual profits.
- Supply-chain and procurement management outsourcing partner to many large corporates, ChainIQ in June this year also suffered a devastating attack, the ripple effects of which impacted multiple customers (UBS, Pictet and Manor so far).
This alliteration is not exhaustive, which is part of the problem. This list of attacks is longer and rapidly getting longer, effectively as this text is being written.
What all the cited attacks have in common is that they also reflect a realization by attackers that the supply chains of private and public sector organizations constitute a massive attack surface. In particular, the supply chain as attack surface also offers an attack vector – and if the supply chain is run as a third-party service by a specialized company it is used as an attack vector-force multiplier.
Looking at this challenge from the perspective of third-party security risk management, third party specialization/concentration almost invariably constitutes a form of elevated risk – in the shape of a risk concentration (e.g. multiple client services outsourced to a single third party), which, conversely, also can coalesce into a single-point of failure risk for a client organization.
Add to this constellation the shift of organizational boundaries under the impression of massively increased use of business process outsourcing from a security risk perspective: the new perimeter is access – your own employees, as well as employees of a third party, whose access privileges may exceed those of your own employees.
Digital and physical supply chains are clearly exposed – and not just to the amorphous hackers, but to commercial, parastatal and state-funded domestic and foreign intelligence collection actors across multiple vectors, i.e. digital, physical and personal. The rise of outsourcing to third parties in business digital and physical supply chains is clearly creating new and in part as yet undiscovered vulnerabilities, up to and including specialization/concentration. That is SaaS that act as force multipliers and such, as having multiple third parties with access inside a client organization’s security perimeter, that at the end of the day potentially increase and certainly facilitate insider threat and risk by an order of magnitude.
Whether the entry point is a software automating passenger baggage management or an element in a productivity software suite, such as Copilot, supply-chains are vulnerable to external and, with even worse effect, internal attacks. Where a single supplier serves a great number of, and can tap into, clients’ digital and physical access rights or manipulate personnel to that end, if breached the services provider becomes a force-multiplier to the attacker. This is particularly true of so-called managed services that concentrate end-to-end outsourced services, not unlike fully comprehensively devised sub-supply chains encompassing a critical business or security function or process.
Conclusion: Meeting the Challenge
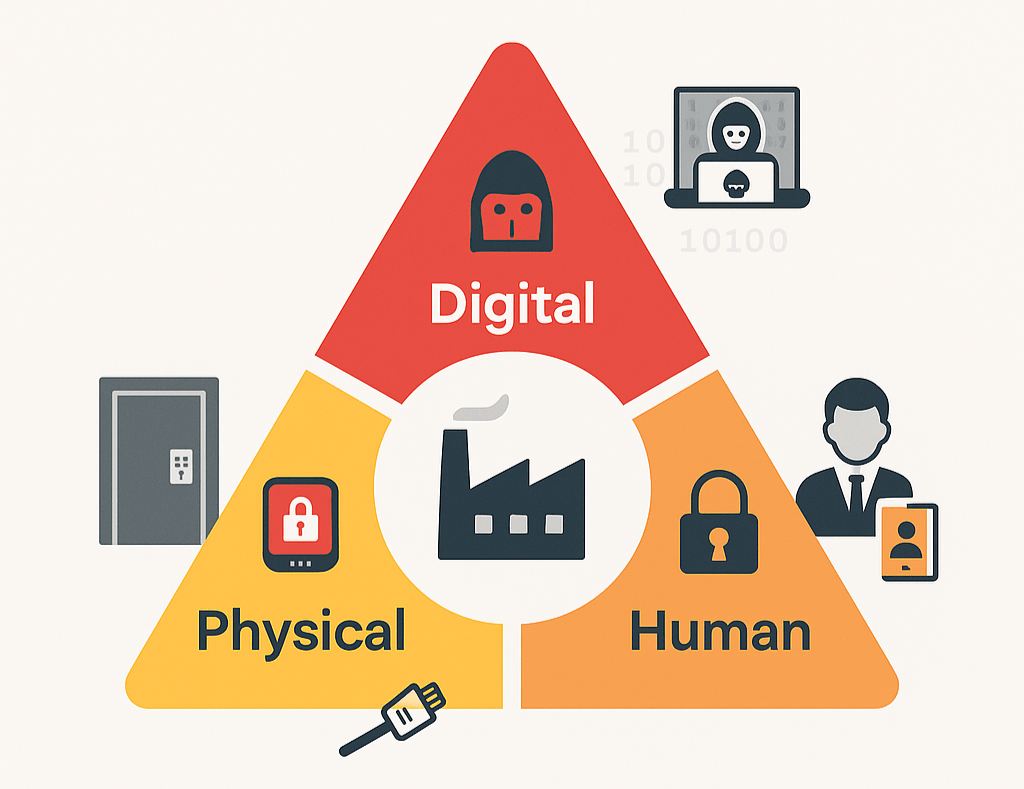
The bottom line is that long before a discussion about means and measures, automation and controls takes place, company leaders should pro-actively pursue a security risk assessment and dialogue for decision-making that engages with plausible scenarios of today’s threatscape. The security posture of an organization should cover more than a single supply chain surface – typically the digital at a singularly high maturity level, because it is currently all the rage.
Discrepancies in maturities between the different security disciplines (digital, physical, personnel) is in and of itself a self-inflicted vulnerability – and as profoundly dangerous at that, as it is avoidable by deliberate enterprise security risk management. There is no point in having state-of-the-art IT security, if anyone can walk into a company’s offices or easily suborn employees or trusted contracted due to an unaddressed toxic workplace culture. Successful security is the result of a collective effort pursued by employing well balanced means that can count on the support of internal and external stakeholders, investors, customers, employees and contractors.
What Can Pragmatica Do For You?
We at Pragmatica offer a hands-on and comprehensive security risk management approach addressing supply chains, third party and outsourcing management.
We are happy to support you with the following services:
- Carrying out a comprehensive risk analysis of outsourcing contracts from the perspective of third-party security risk management
- Security-based Data Transfer Impact Analysis (DTIA) for the assessment of data transfer risks
- Review of additional organizational and technical security measures
- Identification and designation of security risks when outsourcing to cloud providers in third countries
- Creation of a prioritized risk mitigation plan (risk treatment plan)
- Selection of cloud providers that offer the highest encryption standards and ideally are not subject to “compelled assistance” under EO 12333, FISA obligations or similar obligations under administrative law.
What Can Pragmatica Do For You?
We at Pragmatica offer a hands-on and comprehensive security risk management approach addressing supply chains, third party and outsourcing management.
Enterprise Security Risk Management
a tried and proven framework for effectively organizing all security management resources of an organization according to industry good practice.
Third Party Security Risk Management
based on our experience supporting clients – especially on establish an effective/compliant governance and control framework and how to rate, rank, monitor and control third party security risk exposure in contracts and audits.
Insider Threat & Risk Management
including DLP-deployment sourced from proprietary counter-intelligence know-how and benchmarked to meet requirements in regulated and non-regulated industries.
Data Transfer Impact Analysis (DTIA)
with a view to foreign intelligence collection risk – what you need to know about risks and exposure before you entrust your “crown jewels” to a third party with links at home or abroad.
Do you have any questions?
We would be happy to accompany you and your company on the path to security!
Sources
- https://www.cnbc.com/2025/09/21/what-we-know-about-the-cyberattack-that-hit-major-european-airports.html
- https://www.bbc.com/news/articles/cr4q3v9xqk2o
- https://theconversation.com/how-mands-responds-to-its-cyber-attack-could-have-a-serious-impact-on-its-future-and-its-customers-260429
- https://www.securityweek.com/chain-iq-ubs-data-stolen-in-ransomware-attack/
- https://www.dtexsystems.com/blog/2025-cost-insider-risks-takeaways/
- https://www.exabeam.com/resources/reports/from-human-to-hybrid-how-ai-and-the-analytics-gap-are-fueling-insider-risk/
- 20241118-finma-risikomonitor-2024.pdf, cf. p. 16 et seq.
