- Information SECURITY
How the shifting threatscape demands comprehensive security risk management
Cyberattacks on supply chains are long since not isolated case more. What with the recent attack on the widespread baggage management-software Muse from Collins Aerospace began – with Effects on Airports in London, Berlin, Brussels and Dublin – is Part of a threatening Development: A series of targeted Attacks on critical Infrastructures and Supply chains in Europe.
Just a few more examples from the last few months:
- Jaguar Land Rover recently had to halt production – with repercussions that continue to this day.
- A so-called prompt injection attack (“Echoleak”) on Copilotpart of the Microsoft ecosystem, was stopped at the last moment.
- Marks & Spencer suffered an attack on its time-critical supply chain – with an expected loss of around a third of its annual profit.
- The outsourcing service provider ChainIQ was compromised – with consequential damage for companies such as UBS, Pictet and Manor.
These incidents are only the tip tip of the iceberg.
Was alle diese Angriffe gemeinsam haben: Sie treffen Unternehmen über ihre Lieferketten. These are today often high networked, complex and on specialized Third parties outsourced – exactly the makes them to the ideal attack surface.
The risks increase in particular due to:
- Concentration of services on a few providers
- SaaS, cloud and procurement outsourcing without a coordinated security architecture
- Access rights of third partiesthat exceed those of your own employees
- Lack of control over new perimeters – Digital, physical and personnel access channels
Each of these weaknesses can in emergency to the Multiplier for attacker become – with enormous damage.
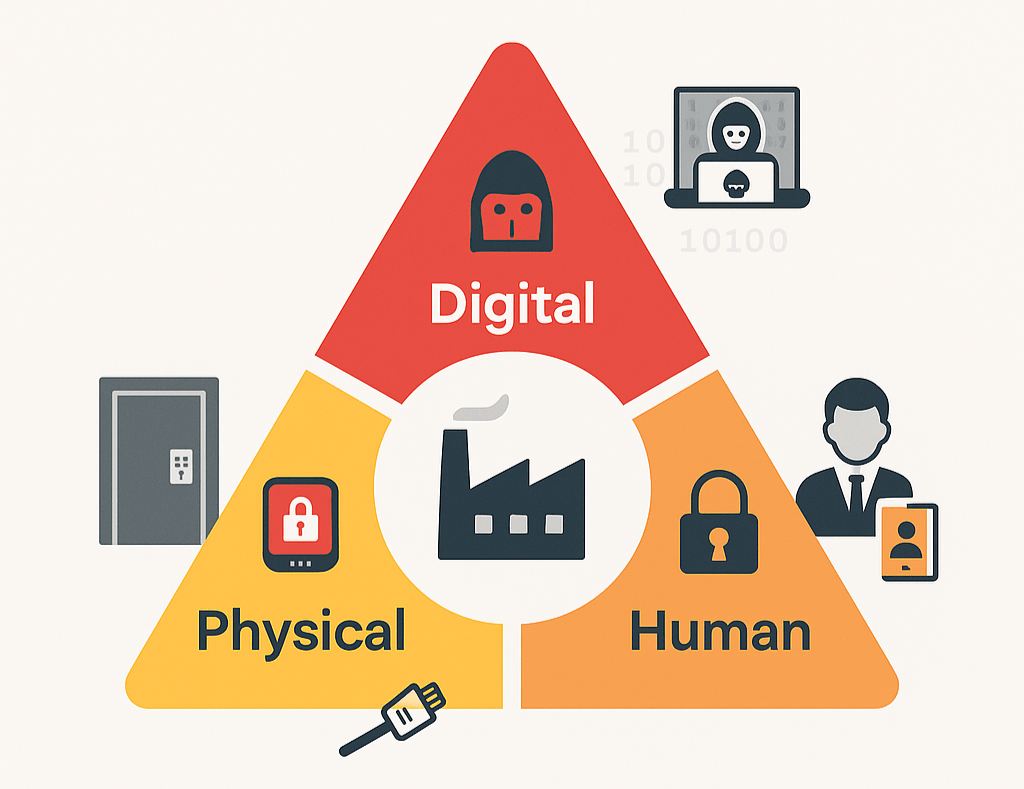
New reality: threats are hybrid
Supply chains are today digital AND physically exposed – affected are not only Data, but also Logistics systems, Locations and People. Cybercriminals, Industrial espionage, state financed Actors – them all use multidimensional attack paths.
Particularly critical: Managed services and third parties with privileged system access. If such a service provider is compromised, this can have a domino effect with massive consequential damage – even for companies with a high security maturity of their own.
Resilience begins with risk awareness
Before talking about technologies, automation or tools, you need a strategic understanding for the new threat picture. The decisive factors are:
- Security assessments of the entire supply chain
- Coordinated third-party risk management
- Coordinated security architectures for digital, physical and personal risks
- Cultural resilience through awareness, leadership and governance
Selective IT security is not enough. Resilience is created through integrated, pragmatic security risk management – strategically, operationally and culturally.
Pragmatica supports you with a proven approach!
With our experience from over 500 projects, we offer a practical approach to comprehensive security risk management – with a focus on supply chains, outsourcing and third party management.
Our services
Enterprise Security Risk Management
Holistic regulatory framework based on best practice for managing all security disciplines.
Third Party Security Risk Management
Evaluation, classification and monitoring of external partners in the context of governance, contracts and audits.
Insider Threat & Risk Management
DLP introduction, awareness and benchmarks based on counter-intelligence know-how.
Data Transfer Impact Analysis (DTIA)
Assessment of outsourcing risks for data transfers abroad - with a focus on government access options.
Do you have any questions?
We would be happy to accompany you and your company on the path to security!
Source reference
- https://www.cnbc.com/2025/09/21/what-we-know-about-the-cyberattack-that-hit-major-european-airports.html
- https://www.bbc.com/news/articles/cr4q3v9xqk2o
- https://theconversation.com/how-mands-responds-to-its-cyber-attack-could-have-a-serious-impact-on-its-future-and-its-customers-260429
- https://www.securityweek.com/chain-iq-ubs-data-stolen-in-ransomware-attack/
- https://www.dtexsystems.com/blog/2025-cost-insider-risks-takeaways/
- https://www.exabeam.com/resources/reports/from-human-to-hybrid-how-ai-and-the-analytics-gap-are-fueling-insider-risk/
- 20241118-finma-risikomonitor-2024.pdf, cf. p. 16 et seq.
